Released in May 2017, Endpoint Protector 5 came with a modern intuitive user interface, significant backend enhancements as well as new features and a completely redesigned and improved eDiscovery module. The upgrade underlined our commitment to continuing to provide great Data Loss Prevention solutions that address today’s data security needs and concerns.
Since then, our development team has been working hard around the clock to boost existing features and add new ones based on user feedback and industry demands. Today, we are happy to introduce our very first update for the 5th version of our flagship product, Endpoint Protector 5.1.0.0. Let’s take a closer look at some of its highlights.
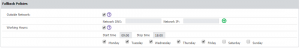
Time and Network based Device Control policies
From this point on, admins will have the option to enable time and network based access rights from Device Control. What this essentially means is that different access rights can be set if a computer is being used outside business hours or outside the company network. Working days and hours can be chosen in the Global Settings section of Device Control. To activate the outside network option, admins have to check the box for it and then list a Network DNS and Network ID. Up to four networks can be added. Once activated, the rules that govern outside hours can be defined in Global Rights.
Keep in mind that, if predefined Standard Device Control Policies are active, the new section governing the fallback policies will not appear. Only those that choose to customize these policies will have access to it.
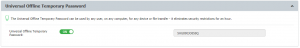
Universal Offline Temporary Password
A new feature added to Endpoint Protector 5.1, the Universal Offline Temporary Password (UOTP) can be used by any user, on any computer, for any device or file transfer, eliminating all security restrictions for one hour. Once it has been used or if there are security concerns raised over it, the password can be revoked. The next time it will be activated a new OTP Code will be generated, making the previous one invalid.
Offline Temporary Password Improvements
The Offline Temporary Password (OTP) section also got a makeover which facilitates the generation of an OTP Code while providing additional options for its parameters. Until recently, OTPs could only be generated for specific devices or/and computers. This has now been extended to users as well, allowing companies more flexibility in the way they manage temporary access rights. An OTP Code can be generated for a specific device, on a specific computer, for a specific user. Alternatively, the OTP Code can be generated for a specific user, for all file transfers, on any computer that employee connects to.
In addition to the predefined time validity periods (from 30 minutes to 30 days), the option to create custom timeframes has been introduced. This means an Offline Temporary Password that has an exact Start and End Date/Time can be generated.
Multiple Administrators Groups
New Administrators Groups have been added for more flexible and customizable admin roles. Along with an improvement of the previously available managed departments, admins can now be granted access to only specific features of the Endpoint Protector Dashboard.
In this way, admins can, for example, monitor activity with reports and analysis without intervening in network-wide policies or gain control over certain sections such as the assignment of Temporary Offline Passwords and Enforced Encryption, which might be granted to helpdesk personnel that need to solve emergency situations.
Automatic eDiscovery Scans
The first update of our eDiscovery module adds additional options for scans. They can now be scheduled in advance for a single, one-time scan or for re-occurring scans, on a weekly or monthly basis, making it much easier for admins to conduct mass network-wide controls at specific intervals.
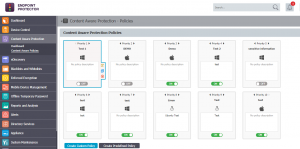
Updated Content Aware Protection
The Content Aware Protection module has been updated to the new user interface, for a smoother creation of policies.
In order to support clients working towards GDPR compliance, a great number of PIIs have been added to cover many more EU countries, among them IDs for Bulgaria, Croatia, Ireland, Italy, Latvia and Lithuania, Luxemburg SSN and VAT ID, Hungary SSN, Slovenia VAT ID etc. PIIs for Peru and Indonesia were also included.
Optical Character Recognition Added
Images can now be scanned for sensitive information as well. An option that allows Optical Character Recognition (OCR) has been added to Endpoint Protector 5.1. It can be enabled by ticking the OCR box found in the Client Settings section of every entity in Device Control (Global, Groups, Computers).
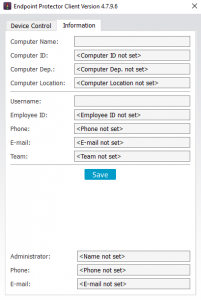
Improved Endpoint Protector Client
The Endpoint Protector Client also received an update. The interface now comes with easier Offline Temporary Password requests and device authorization processes. Whenever a user sends a request to an admin, an automatic email will be generated that includes information about the computer, user, device (Name, VID, PID, Serial Number), as well as a mandatory justification they have to enter. Justifications can later be used for auditing purposes.
A new Information tab has been added to the EPP Client so users can fill in additional details concerning their computers, Employee ID, teams, location and contact information. While this information can be filled in by Endpoint Protector administrators through their dashboard as well, by giving users the possibility to write it in themselves, it can be easily checked for accuracy and kept up to date at all times.
The 5.1 update is available on the Endpoint Protector Dashboard in Live Update. You can find the full list of features available in version 5.1.0.0 in the Release Notes. If the update has piqued your interest and you’d like to know more, you can schedule a demo to discuss our existing and new features with our team of experts.
Download our free ebook on
Data Loss Prevention Best Practices
Helping IT Managers, IT Administrators and data security staff understand the concept and purpose of DLP and how to easily implement it.