Just by looking at the blog post title, it’s easy to understand that we’re talking about computers and confidential data. However, for those that vaguely remember the terms and are more up to date with the latest episodes of The Walking Dead, let’s do a quick refresh and get on the same page. We’ll also get to see what the terms mean right now and what the future will bring, how the human factor can’t be ignored and last but not least, touch on some social engineering.
Relation between bots, botnets and zombies
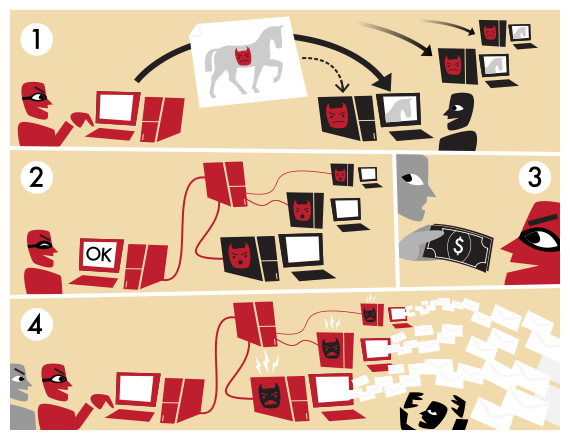
Typically, a bot can be considered a script, malware or a type of application that is designed to execute specific automated tasks which would be too time-consuming for an actual person. Being “fun loving people”, they tend to gather and socialize, creating botnets. Since a botnet can be made up of computers all over the globe, they do not gather in the same place. However, they are actually referred to as zombies because once they are infected, they can be remotely controlled, without the computers’ owners ever noticing (a possible sign would be the computer’s slowness with no apparent reason).
What are botnets used for?
There are several ways cybercriminals can use bots and have financial gains out of them. Some of the most commonly known ones are:
- Botnets can be used for spamming and phishing, or various other tricks in which the unsuspecting internet victim loses some money
- DDoS (Distributed Denial of Service) is also a popular way to go, especially if it’s part of a much bigger plan
- For those that prefer a less challenging environment, leasing the zombies to someone that wants to take them out for a spin is another great way to go
- Since bots can also collect information from the computers they infect, they can be used to steal identities and other confidential data (remember this one as we’ll be getting back to it later on)
Isn’t this old news?
Yes and no. The days when botnets like Rustock, which was disabled back in 2011 and was responsible for 30 percent of the global spam at that time, are behind us. Nonetheless, Qbot, discovered in 2009, received an update sometime in December 2015 / early 2016 and is more sophisticated than ever. The New Qbot has mainly targeted US public institutions like schools, universities, government networks and healthcare organizations, so it’s easy to imagine the type of date it gathered.
However, there’s a new type of bot out there and it could be a story of a bad bot turned good. It looks like it’s here to make up for some of the bad things previous bots have done.
New generation of bots
Remember mIRC? Remember the bots from there? Some were bad, some were harmless and some were good, helping us enjoy a game of trivia. Now remember how we have Facebook, Twitter and various other chat apps? Yes, you guessed it, there’s an app bot for that, or there will be.
We’re able to order pizza via Twitter just by sending an emoji, so with announcements that more and more apps are going to introduce bots to make our lives easier, we’re opening the doors a bit wider to the future. With bots already responsible for an important part of the traffic in the world, let’s step into the future.
Bad bots, good bots, and humans
Reports show that in 2015 humans took back the Internet. Yes, we got back the 1% of online traffic to barely make us the majority. They also showed that while humans are stepping up, the good bots just don’t seem to be keeping up with the bad bots and the humans. The good news is that in this reports we’re mainly looking at the old type of bots and not factoring in the good little bots bees that are going to make all our apps and communication much easier.
2016, the year of the bots
If you take a look around the Internet, you will see various topics that seem to give 2016 to the bots. Companies like Slack are looking at chat-as-platform as a major next step while Facebook is using Messenger and WhatsApp to extend the no client-side and get into the platform game.
Consumers seem to be looking for something else, the next best thing, instead of more apps. Services with bots on the front-end can theoretically be more personal than apps. Add to this the conversational apps moving into various other industries like news, entertainment, and travel, we’re seeing a mixed environment of apps and bots competing with companies like AirBnB and Tripadvisor. They will provide just the right information, add a more human touch to the experience and, just like Siri and Google Now, we will learn to love and trust them.
Enter the Nigerian Prince and his bot
Did you forget about the Nigerian Prince that is about to send you all that money any day now? We’re finally getting to the social engineering part and data loss.
The Prince already managed to earn some of the people’s trust by appearing to be genuinely interested in just make a better living for everybody and spread some money around. So what happens when he’s going to turn into a bot and get some prime real estate in one of your favorite apps that you trust? You know he’s got the money to do anything and again, he’ll appear genuinely helpful. What would be the type of information you’ll be willing to share with him just to catch the last buss or flight, get the best offer on the vacation resort you want to go to? He’s obviously good with money and knows a lot of people so he might be able to provide some really solid business advice. Will you share your customers’ data bases or leave him alone in the background to go through your bank accounts? Why not also provide every type of personally identifiable information or healthcare records you have? I’m guessing you’re not really looking to do that.
Let the good bots help, use technology and avoid data loss
So, by now, we all agree that good bots will help make the future a much better place for us. We can’t just ignore all the benefits and push everything back in the box. But what is the solution to take advantage of everything while keeping our data safe?
While AV solutions can help in getting some of the older generation of bad bots off your computers, it will not really help keep that confidential data safe. You also can’t completely stop using apps and the collaboration tools that will definitely help with productivity in a more and more competitive business environment.
Data Loss Prevention solutions could help with exactly that. They will let us, humans, take advantage of various applications while being there to notify, and if needed, stop us when we’re a bit too eager or unknowingly share all that valuable sensitive data.
So what solutions to look for?
2016 might belong to the bots but let’s face it, the decision of what we need and what to get, still belongs to us. Those in charge are still the people after all and not just a bunch of zombies.
As mentioned above, apps are saturating people’s lives and we’re seeing the shift to a different approach, more OS dependent. With this in mind, look for a DLP solution that is able to provide the same features for Windows, Mac OS X, and Linux, while also providing Mobile Device Management and keeping an eye on all the iOS and Android tablets and smartphones.
The future looks really interesting in terms of mobility and automated services. Stay close as we continue to provide solutions to keep confidential data safe while also allow you to take advantage of all the latest technology developments.
Download our free ebook on
Data Loss Prevention Best Practices
Helping IT Managers, IT Administrators and data security staff understand the concept and purpose of DLP and how to easily implement it.
















