In today’s digital landscape, data exfiltration has become increasingly concerning, with successful cyberattacks highlighting its severe impact on organizations and individuals. High-profile data incidents have shaken major businesses, as well as society, exposing flaws in cybersecurity defenses. These cyber-threats highlight the unsettling truth that criminal organizations aggressively seek and exploit sensitive data for illicit gain.
Over the last decade, some of the biggest-ever cases of data exfiltration have shaken the corporate world. Equifax suffered a data breach in 2017, affecting around 145.5 million clients, with stolen data including Social Security numbers, birth dates, and other sensitive information, resulting in a $675 million customer settlement in 2019. In 2019, Capital One disclosed a data breach that affected around 100 million Americans and 6 million Canadians, with stolen information including names, addresses, and credit scores. This violation resulted in a $190 million settlement in 2022. Yahoo’s 2013 data leak, discovered in 2017, affected a staggering 3 billion accounts, resulting in a $350 million reduction in its selling price to Verizon.
What is Data Exfiltration?

Data exfiltration refers to the illegal removal of sensitive or secret information from a secure system. In simple terms, it means intentionally gaining access to sensitive data with malicious intent. Criminals can do that in a variety of ways, such as through discovering and exploiting vulnerabilities and flaws in security systems, employing malicious software, ransomware attacks, duping people with scams, or even obtaining assistance from insiders with access to the data.
There is a major difference between the terms data exfiltration and data breach – a data breach happens when data is exposed or accessed without forceful and intentional removal from the system. In data exfiltration, the emphasis lies on the deliberate extraction of data from its original location. Another related term is data leakage, which has the same consequences, but the cause is purely accidental. For example, a data breach would occur if a misconfigured search database was publicly available and accessed, a data leakage would occur if someone unintentionally shared the URL of this publicly available database on social media, whereas data exfiltration would occur if the same database was protected and a criminal hacked into the system to copy its content.
The term data exfiltration (also known as data extrusion or data exportation) can also refer more specifically to techniques used by criminals to transport data out of a system to which they have previously gained access. In this scenario, the term data infiltration refers to the actual act of acquiring access to the system; the criminal first invades the system, acquires access to the data, and then takes it from the system by copying it to their own devices.
How Does Data Exfiltration Occur?
Data exfiltration can be accomplished through a variety of means. Here are some of the most prevalent ways used by everyone from solitary malicious hackers seeking to impress their community to nation-sponsored big criminal organizations specializing in cybercrime:
- Phishing and other types of social engineering: By far the most prevalent method of gaining unauthorized access to sensitive material is to trick an innocent individual into assisting. Phishing attacks and social engineering allow criminals to obtain account information, which they subsequently use to gain access to the system and start the exfiltration process.
- Malware and ransomware: The second most common way is to distribute harmful software that either steals system login information, acts as a conduit for the attacker to access the victim’s computer and subsequently other internal company systems, or simply copies the entire storage content and encrypts the media to allow for random demands.
- Exploiting security flaws: These flaws can be as simple as legitimate users using weak and easily broken passwords, or the same or similar passwords across several systems. In such circumstances, data is essentially handed to the criminal on a platter. Other examples of exploitation include organizations failing to patch their systems and the attacker gaining access to them via well-known and publicly available exploits for network and web vulnerabilities.
- Theft of removable media: Even a highly skilled hacker may take advantage of an opportunity to make their life simpler if they can merely steal a victim’s USB drive. Such removable media as USB drives or portable disks may contain not just the data itself, but also crypto keys, password files, or other tools that allow the criminal to continue the attack.
- Unauthorized device access: Similar to portable media theft, this is a method used by cybercriminals to make their lives simpler. An insecure device such as an unlocked cell phone lying around in a cafe, or even an unprotected switch that the attacker may connect to without authorization, usually grants the attacker significant access privileges that can be utilized for massive data exfiltration.
- Network eavesdropping: In the age of remote work, our attention is once again drawn to networks. Without adequate network access control, such as RADIUS-based zero-trust network access (ZTNA), an ex-employee can simply connect to the company’s internal resources and exfiltrate data. As a different example, a remote worker operating from a public hotspot without a protected VPN may be an excellent candidate for a targeted sniffing assault by a criminal spoofing the hotspot network.
Five Types of Data Exfiltration
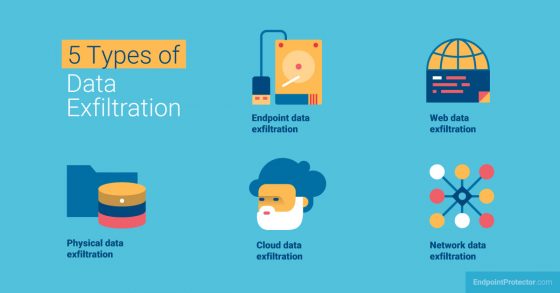
There are five basic types of data exfiltration techniques based on the layers used to access the data sorted from the most concerning to the least common. These types also demonstrate that the company’s security policy must cover all bases.
- Endpoint data exfiltration: This type of data exfiltration occurs when data is accessed through an endpoint, such as a company user’s computer. This, however, goes much beyond simply physically accessing the device itself. Endpoint data exfiltration can occur as a result of an employee opening a phishing email, visiting a bogus page, and providing their credentials. As a result of the plethora of social engineering techniques aimed at endpoint users, endpoint data exfiltration is the most prevalent form.
- Web data exfiltration: The web’s tremendous popularity, along with the ease of creating custom applications, makes this technology a very appealing bite for hackers. Web technologies are rife with flaws, and custom applications are frequently built without security in mind. Additionally, web apps are now employed as front-ends for even the most sensitive datasets. Any attack involving web vulnerabilities and misconfigurations can result in web data exfiltration.
- Physical data exfiltration: Physical security is still a big problem in today’s globally interconnected world. Data-carrying devices and media are small, light, and simple to misplace, abandon, or steal. While a stolen laptop or smartphone can be easily disconnected from the company network, and often takes some time to hack into, a stolen thumb drive is most often unencrypted, so the data on it is immediately accessible to the criminal.
- Cloud data exfiltration: The cloud’s entire concept is predicated on sharing the same space with others. Many virtual systems use the same physical servers, and each virtual system may include compartments for different businesses and individuals. While the technology isolates these rather well, it is still possible to misconfigure cloud storage environments, making information easily accessible to outsiders. As a result, SaaS adds another layer of concern to security teams.
- Network data exfiltration: This includes any strategies used by the criminal to obtain access to the company’s networks and then escalate the attack from there. This could be due to a lack of wireless network access control, such as using simple password authentication on company Wi-Fi networks, sniffing a public connection without a VPN, or even the attacker posing as a technician and physically connecting their device to a switch without Network Access Control (NAC).
Who is Behind Exfiltrating Data?
While the value of sensitive data to the organization is evident, it may be difficult to fathom what benefits a criminal might get from accessing such data. After all, thieves are usually seeking money, so how can they profit from data exfiltration? Unfortunately, many shady entities are willing to pay enormous sums of money to malicious threat actors for stolen valuable data.
The sensitive data buyer can then utilize it for a variety of purposes. Personally identifiable information (PII), such as combinations of names, addresses, and Social Security numbers, enable criminals to attempt identity theft and, for example, obtain large financial credit in the name of someone whose data was stolen.
Another type of sensitive data often affected by exfiltration is a company’s intellectual property or trade secrets, which is frequently a tasty treat for competitors. In some cases, even a small amount of data may be extremely valuable. If a company, for example, gains access to its greatest competitor’s secret formula, it might represent a significant shift in its technologies, allowing it to capture a larger share of the market.
Last but not least, there is politics involved. Both the Yahoo! and Equifax incidents were discovered to have been at least partially carried out by malicious actors representing two major powers that are not particularly fond of the United States. Weakening a country’s economy through data exfiltration is a common occurrence in cyber-warfare, and given the current state of global affairs, we can only anticipate it to become more of a threat in the future.
Insider Threats and Data Exfiltration
In addition to technological flaws, human flaws increase the risk of data exfiltration even more. Insider threats are a typical occurrence in even the most serious data exfiltration scenarios. After all, the Capital One perpetrator was an ex-Amazon employee who exploited Amazon technologies to carry out her attack.
Internal threats can be divided between those who act intentionally and those who are just instruments of others. Malicious insiders could include current unhappy employees enticed by money from a dubious competitor, or even an ex-employee who, due to technological flaws, still has access to the company network.
Unintentional insider threats are significantly more widespread, and this covers all human errors as well as, for example, the user activity of social engineering victims. By falling for a ruse, such people unwittingly become security risks and even accomplices in a crime. And, no matter how hard you train your staff not to fall for such scams, there is always the possibility that the attacker will outwit them.
The Impact of Data Exfiltration
Data exfiltration can have a far-reaching impact on businesses, victims, and society as a whole. Such impacts go way beyond the direct consequences and may linger for many years after a data exfiltration incident.
Impact on organizations
The greatest initial effect of data exfiltration is on the crime’s direct victim: the hacked organization. To begin with, the company’s image is always seriously damaged in such cases – clients are very likely to be less comfortable dealing with the company if they believe their data is not adequately protected.
Depending on the industry and the type of company data stolen, the hacked company may also suffer legal implications based on laws such as GDPR, as well as lose essential licenses or have to devote a significant amount of time and effort to show that they are still fit to continue business in a controlled environment. Such impacts are the most severe in industries such as healthcare, banking, and healthcare with strict regulations against the unauthorized transfer of data, such as HIPAA and PCI-DSS.
Last but not least, the indirect victims who are the owners of stolen data deserve compensation because their personal information is quite likely in the hands of a criminal organization and could be used against them. These types of cases are usually settled by victim compensation, which can reach exorbitant proportions for even the largest corporations, significantly hurting their financial flows.
Impact on the Data Subject
Data exfiltration has a significant influence on the persons whose information has been stolen. It may result in identity fraud and catastrophic implications such as engagement in uncommitted crimes. It is also possible that the data will be used against them for extortion or blackmail. Last but not least, it may have a direct impact on their finances if, for example, a stolen credit card number is used for fraudulent activities shortly following the data theft.
The most concerning aspect of this impact is that the victim never knows if and when they will be affected. In many circumstances, there is nothing they can do to protect themselves – they can change their phone number but not their home address or name. Moreover, despite any instructional campaigns by the compromised organization or even the public media, they may be oblivious to the threat or lack sufficient technological understanding to comprehend what is at stake.
Impact on the Society
The more data is exfiltrated and the bigger the victims, the greater the societal impact of these incidents. Many people are already uneasy about storing their personal information in huge systems like social networks. If people do not feel comfortable in the digital realm, society’s digital developments are likely to reverse. Who knows, maybe in 50 years we’ll all be using cash again since no one will trust cashless transactions.
Simultaneously, in the face of data exfiltration, society must safeguard itself in any manner possible. And the best way is to impose stronger security regulations on all organizations that store sensitive information about individuals. Such stringent standards, however, have a significant influence on the expenses for organizations, which must invest in multiple technologies, establish security systems, and recruit security experts. Ultimately, it is the end customer that pays the price.
Data Exfiltration Prevention Techniques
Every aspect of the organization’s security policies and systems contributes to the prevention of data exfiltration. Some, however, are more significant than others for this specific purpose.
- Encryption: If only one technology or strategy could be chosen to mitigate the damage of data exfiltration, it would undoubtedly be encryption. Data should be stored in encrypted form, transmitted through encrypted channels, and only decrypted by the recipient after making sure they are legitimate, for example, through the use of certificates, digital signatures, biometrics, and other methods. What is critical to realize is that encryption protects the data, not the system. Its purpose is to ensure that if the system is compromised and data is stolen, the thief can do nothing with the data.
- Strong authentication and access control: Too many instances of data exfiltration are due to trivial factors such as a user with an 8-character password based on their child’s name and year of birth, which can be cracked in minutes, even if it is comprised of uppercase, numerals, and special symbols. Strong authentication methods include complex long passphrases, combined with MFA, biometrics, and physical devices like security dongles. However, even the strongest authentication is useless if users can access too much. Systems managing sensitive data should approach access control from a zero-trust perspective, providing every user only the absolute minimum required permissions.
- Segmentation: If a criminal gains access to the system for the aim of data exfiltration, it is immensely advantageous if they find themselves in a closed “room” and are unable to access other such “rooms” belonging to the company. This goal is met by system and network segmentation. Even if the attacker gains access to one system or network, they are unable to access other systems or networks. Such a goal is achievable using the lowest layers of the network, such as VLANs, traversing which is a practical impossibility.
- Education and awareness: While the effectiveness of phishing detection campaigns and training in organizations is difficult to assess, it is a critical step to ensure that everyone in the company is aware of the risks and will most likely not fall for the most blatant social engineering ploys. However, this precaution is insufficient on its own, because a determined attacker can go to great lengths when, for example, impersonating a superior to gain access to a critical system.
The Role of Data Loss Prevention (DLP) Solutions
Data Loss Prevention (DLP) technologies were created from the ground up to assist in protecting organizations from data exfiltration through the most volatile channels. If a company wishes to invest in the technology that will provide the greatest degree of data security, it will almost certainly choose DLP.
Other security solutions safeguard particular pathways and assist in the prevention of specific types of data exfiltration attacks. A Zero Trust Network Access (ZTNA) solution, for example, will secure the corporate network against unauthorized access, but it will not protect the company’s website. A firewall protects against some network-based attacks but does not affect the content of legitimate network traffic such as outbound emails or web communications. DLP is there to help when all of these early prevention solutions fail – once the attacker is already “in” in some fashion.
DLP focuses on the data itself rather than how it is accessed. DLP is there to make it impossible for this data to leave the system. It is effective against physical data exfiltration because it prevents sensitive data from being copied to an external device. It is effective against endpoint data exfiltration since it prevents the user from copying data into an email as part of a social engineering attempt.
Endpoint Protector for Data Exfiltration Prevention
While there are many DLP solutions on the market, one stands out if you want complete and simple protection. Most major DLP solutions are notorious for being too complex in their configurations, making them difficult to use efficiently. The trend of including DLP as part of other specialized security solutions undermines DLP’s entire objective, which is to focus on the data rather than how the data is handled. Endpoint Protector by CoSoSys assists in covering all bases in real time while keeping things simple enough to provide a quick return on investment.
Endpoint Protector’s Device Control offers granular control over USB and peripheral ports to help mitigate risks associated with physical data transfer. Content Aware Protection scans the content and context of data transfers, ensuring that critical information, such as personal identifiers or financial details, is not exfiltrated. Furthermore, the application control feature restricts data transmission through potentially vulnerable applications, including cloud storage and email clients. eDiscovery plays a pivotal role in identifying and addressing data exfiltration activities, backed by real-time monitoring and alerts that prompt immediate action against suspicious activities. The solution also ensures data remains unreadable to unauthorized parties by using Enforced Encryption on data in transit. Integrating seamlessly with existing IT infrastructure, Endpoint Protector not only protects against data exfiltration but also reinforces the overall data security posture of an organization.
Schedule your demo here.
Download our free ebook on
Data Loss Prevention Best Practices
Helping IT Managers, IT Administrators and data security staff understand the concept and purpose of DLP and how to easily implement it.
















