A persistent myth haunts all Data Loss Prevention (DLP) solutions: the belief that its deployment will be a slow and cumbersome process that will stretch across months, likely to affect both a network’s speed and employees’ productivity. The reality though is quite different: most DLP products nowadays aim for efficient deployment, with some taking only minutes to set up, a far cry from the months being floated around the collective imagination.
Endpoint Protector for example was created with flexibility and fast setup in mind, enabling companies to get down to the serious task of protecting their data in record time. In fact, it can be up and running in 30 minutes or less and those are not just empty words that sound good splashed across a banner ad: they are a verifiable statement.
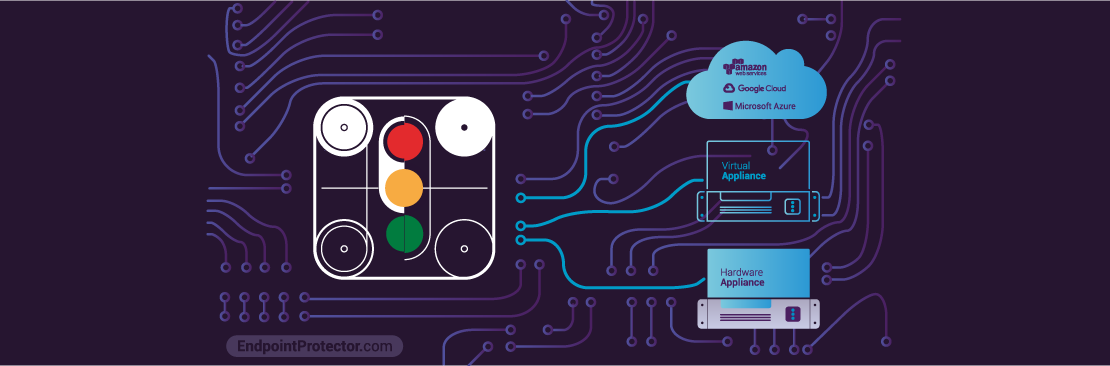
Part of the reason for this is the multitude of deployment options Endpoint Protector offers. From classical hardware appliances to the latest Cloud Services, businesses can easily choose which method is best suited to their existing infrastructure. Let’s have a closer look at what the options are and when they should be used!
Riding the Cloud Wave
Since its widespread adoption, cloud computing has revolutionized IT and software systems delivery with many applications now running in the cloud. Data centers have supplanted on-site servers, providing both a higher level of protection and a distributed service that ensures a level of resilience a modest IT budget is unlikely to provide.
Cloud providers also offer a degree of flexibility and scalability that traditional IT infrastructure lacks: pricing tiers charge users only for the resources they use rather than a flat-fee for services they might potentially use. By using cloud computing, companies no longer need to deploy their own resources or allocate IT staff to manage services internally but can rely on cloud service providers for both.
At Endpoint Protector, we work together with our customers to constantly improve our solutions not only when it comes to their functionalities, but also to their deployment and support. With the rising use of cloud services, we expanded our deployment options to include various cloud service providers such as Amazon Web Services (AWS), Microsoft Azure or Google Cloud Platform (GCP) to meet the needs of companies that have taken the plunge into cloud computing.
This deployment option naturally requires a preexistent cloud account and an understanding of how these services work to ensure a smooth integration and deployment of Endpoint Protector in the cloud.
Taking things Virtual
Virtual appliances have fast become our most popular deployment method for Endpoint Protector. Suitable for companies of all sizes, they are available in multiple formats, being compatible with the most popular virtualization tools such as VMWare Player, VMWare Workstation, Microsoft Hyper-V, Oracle VirtualBox, etc.
The Endpoint Protector Appliance just needs to be installed in a Virtual Environment, its licenses imported and its client deployed to endpoints across the company network. It all takes 30 minutes or less and it is easy to scale: companies can license the exact number of computers they want to protect. Due to its user-friendly web-based interface, it also offers a short learning curve.
Keeping it Old School
For companies that have not yet adopted the latest virtualization tools or cloud services, Endpoint Protector still offers the possibility of deployment via Hardware Appliance. Protecting networks with more than 15 computers, our Hardware Appliances come with everything preinstalled, with different models available based on a company’s organizational needs.
There is no installation required when using a Hardware Appliance. Administrators just need to turn on the appliance, assign an IP in the local network and deploy the Endpoint Protector client on the company’s computers.
Hardware appliances are for companies that prefer having on-premise dedicated hardware. And while they require a minimum workload for deployment and management, they lack the degree of flexibility and scalability offered by virtual appliances and cloud services.
Data Loss Prevention in 30 minutes or less
Using any of these three methods guarantees a smooth, hassle-free deployment of Endpoint Protector, with minimal effort and a short learning curve. Whether companies are already using cloud services, a virtualization tool or want a piece of additional hardware in their office, Endpoint Protector is here to ensure that all their needs are met and that tiring, time-consuming DLP deployments remain in the realm of the imagination where they belong.
Download our free ebook on
Data Loss Prevention Best Practices
Helping IT Managers, IT Administrators and data security staff understand the concept and purpose of DLP and how to easily implement it.