Starting with macOS 12.0, Apple requires more information from the CA certificate.
To make Deep Packet Inspection work on macOS 12.0 or higher, a CA certificate that contains more information is needed.
To obtain this certificate that includes more information, Force server certificate stack setting that regenerates the CA and the Server Certificate Stack was implemented.
This new setting is valid for macOS 12.0 or higher, but macOS 11.0 (and higher) also uses a CA Certificate. Therefore, after regenerating the CA certificate, ensure that it is downloaded again for macOS 11.0 (or higher) and added to System -> Keychain Access.
This impacts ALL certificates that are already used. In this case Self Signing Certificate is replaced and has to be configured again from the Endpoint Protector Server -> Server Maintenance -> Self Signing Certificate.
Follow the next steps if you want to use Deep Packet Inspection on macOS Monterey and also the Self Signing Certificate:
1. Go to System Settings -> Server Certificate Stack.
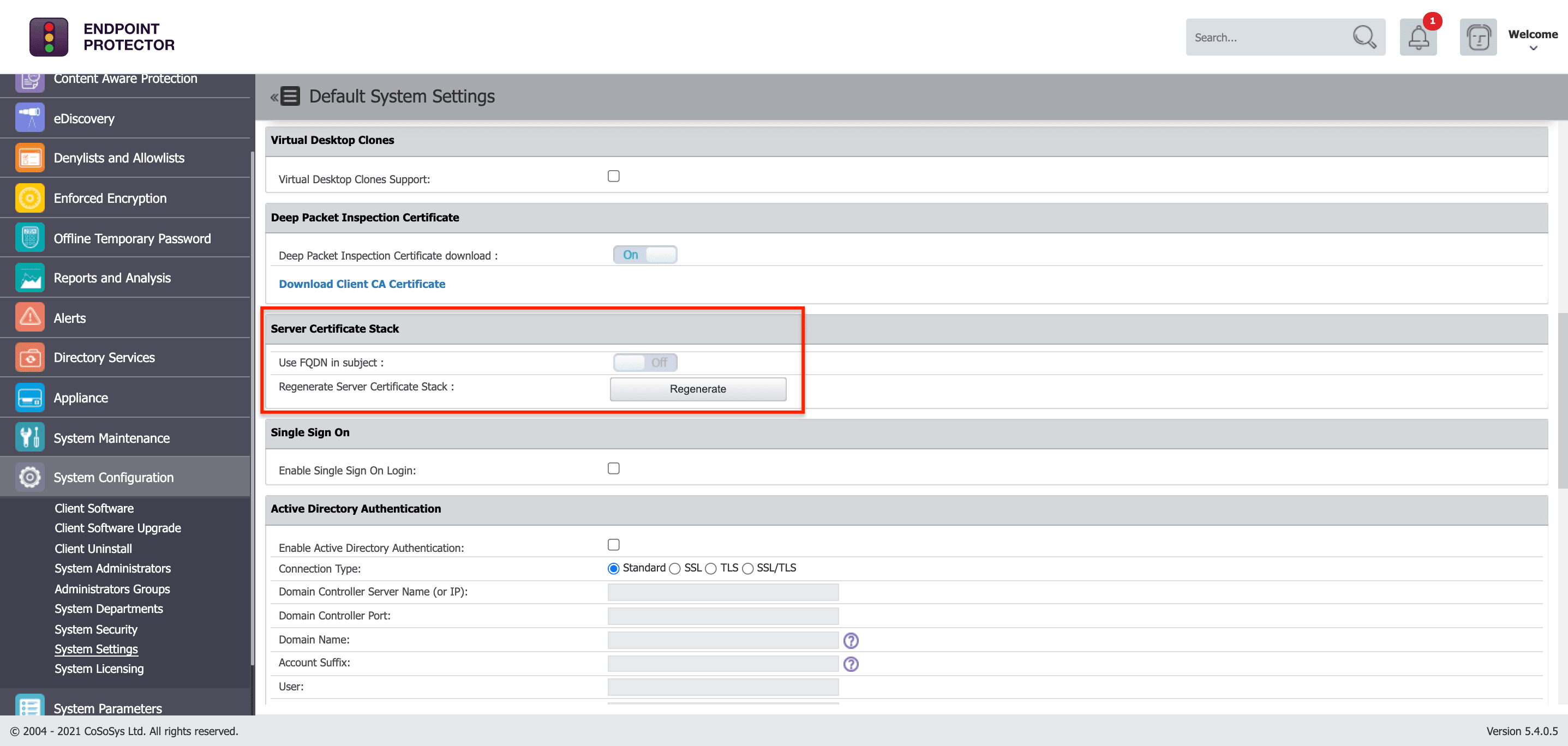
2. Hit the Regenerate button.
3. Wait until the server certificate is regenerated and you have to re-login on the page. As a result of the previous action, Self Signing Certificate is replaced with the server one.
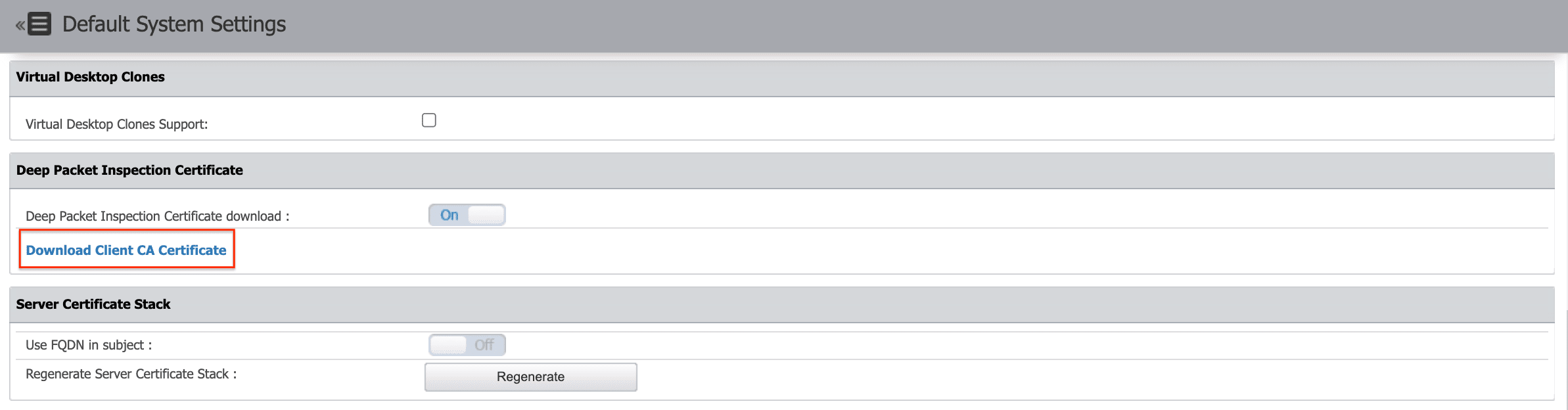
4. Go to System Settings -> Deep Packet Inspection Certificate.
5. Hit the Download Client CA Certificate.
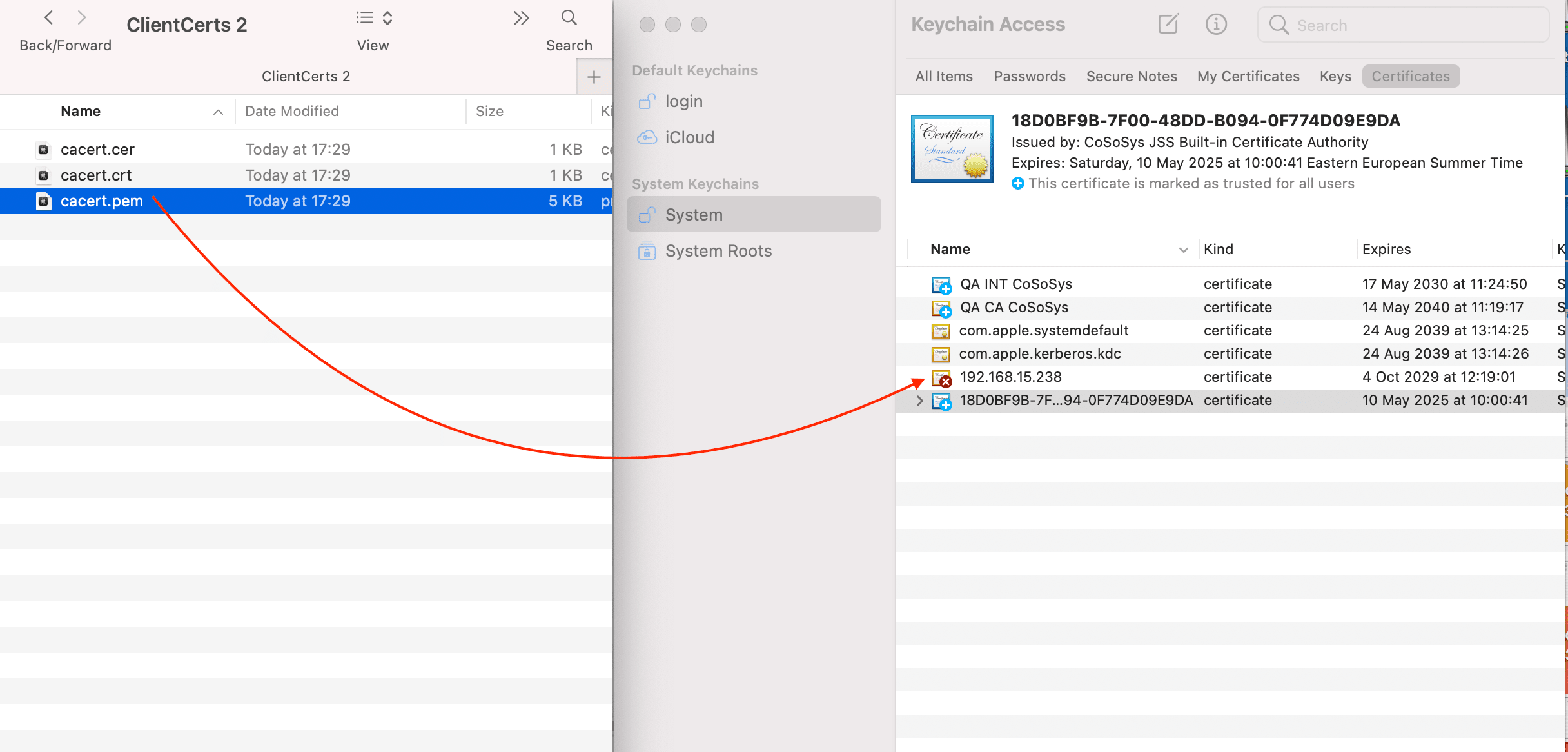
6. Add the newly downloaded certificate in Keychain Access -> System.
7. Always Trust the new certificate.
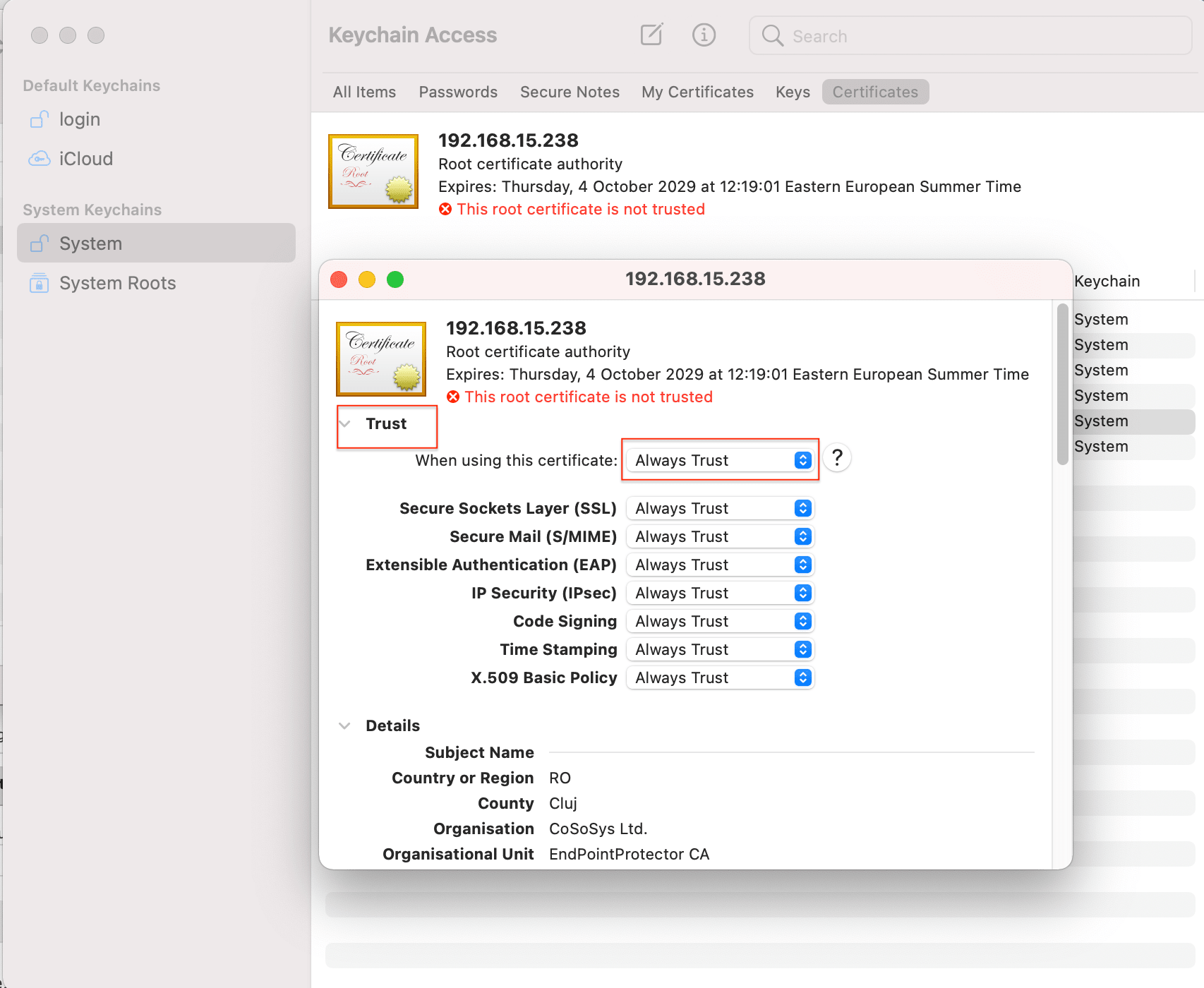
8. Deep Packet Inspection is working now on macOS Monterey.
9. Go to Appliance -> Server Maintenance -> Self Signing Certificate
10. Set up a new Self Signing Certificate.
11. Save.
12. Deep Packet Inspection should work with the new self-signed certificate in place.
Note
Every time the Regenerate button is hit, the Self Signing Certificate must be imported once again.
Regenerating the Server Certificate Stack affects also the certificates that are used on Windows.